SaintForLife
Well-known member
Offline
It looks like the first shoe has dropped with the Durham investigation with the Clinesmith plea deal. Clinesmith wasn't a low level FBI employee involved in the Crossfire Hurricane investigation.
He worked with Strzok to arrange sending an FBI agent into Trump-Flynn briefing, was on the Mueller team, he took part in the Papadopoulos interviews, and he participated in the FISA process.
From the NYT article:

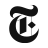 www.nytimes.com
www.nytimes.com
I wonder who else knew about the lies?
He worked with Strzok to arrange sending an FBI agent into Trump-Flynn briefing, was on the Mueller team, he took part in the Papadopoulos interviews, and he participated in the FISA process.
From the NYT article:

Ex-F.B.I. Lawyer Expected to Plead Guilty in Review of Russia Inquiry (Published 2020)
Prosecutors did not reveal any evidence of the kind of broad anti-Trump conspiracy among law enforcement officials that the president has long alleged.
I wonder who else knew about the lies?